Should make examinations interesting. Apparently, an open-ended SIM that can be either postpaid or prepaid account without the need to change SIMs but still switch between carriers. Either Apple intend to go for their own IMSI (thus become an operator) or the IMSI will need to be updated OTA...hmmmm
"If you are among the millions who will purchase one of the 4G versions of the new iPad Air 2 or iPad mini 3 tablets from Apple in the next few months, and you live in the US or UK, then when you switch the tablet on for the first time, you will find a nano-SIM card already installed in the SIM card slot."
..............
"What Apple envisions with its SIM is that users will be able to quickly and easily switch between different carriers to take advantage of the best short-term deals available at any given time - without having to go through the hassle of getting a new SIM card.
"Obviously, if you have signed up to a two-year contract you won't be switching deals that often, but if you are on a pay-as-you-go deal, then this could be a real money-saver......."
Quotes from:
http://www.ibtimes.co.uk/apple-sim-how-does-it-work-end-sim-cards-1471065
Examination and Evidence from SIM and USIM Cards.
Wednesday, October 29, 2014
Sunday, March 16, 2014
Test your USIM knowledge
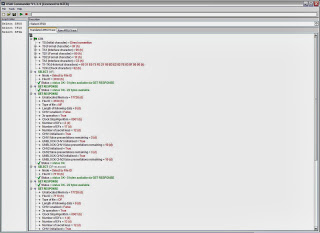
Below is UST (USIM
Service Table) 3GPP 31.102 that may be found in a UST elementary file.
QUESTION 1
There are at minimum 1,900 items for examination discovery, investigatory leads and evidence that can be obtained from these UST entries. Can you identify just 50 items for examination discovery, investigatory leads and evidence? If so, what are they?
Service n°1: Local Phone Book
Service n°2: Fixed Dialling Numbers (FDN)
Service n°3: Extension 2
Service n°4: Service Dialling Numbers (SDN)
Service n°5: Extension3
Service n°6: Barred Dialling Numbers (BDN)
Service n°7: Extension4
Service n°8: Outgoing Call Information (OCI and OCT)
Service n°9: Incoming Call Information (ICI and ICT)
Service n°10: Short Message Storage (SMS)
Service n°11: Short Message Status Reports (SMSR)
Service n°12: Short Message Service Parameters (SMSP)
Service n°13: Advice of Charge (AoC)
Service n°14: Capability Configuration Parameters 2 (CCP2)
Service n°15: Cell Broadcast Message Identifier
Service n°16: Cell Broadcast Message Identifier Ranges
Service n°17: Group Identifier Level 1
Service n°18: Group Identifier Level 2
Service n°19: Service Provider Name
Service n°20: User controlled PLMN selector with Access Technology
Service n°21: MSISDN
Service n°22: Image (IMG)
Service n°23: Support of Localised Service Areas (SoLSA)
Service n°24: Enhanced Multi Level Precedence and Pre emption Service
Service n°25: Automatic Answer for eMLPP
Service n°26: RFU
Service n°27: GSM Access
Service n°28: Data download via SMS-PP
Service n°29: Data download via SMS CB
Service n°30: Call Control by USIM
Service n°31: MO-SMS Control by USIM
Service n°32: RUN AT COMMAND command
Service n°33: shall be set to '1'
Service n°34: Enabled Services Table
Service n°35: APN Control List (ACL)
Service n°36: Depersonalisation Control Keys
Service n°37: Co-operative Network List
Service n°38: GSM security context
Service n°39: CPBCCH Information
Service n°40: Investigation Scan
Service n°41: MexE
Service n°42: Operator controlled PLMN selector with Access Technology
Service n°43: HPLMN selector with Access Technology
Service n°44: Extension 5
Service n°45: PLMN Network Name
Service n°46: Operator PLMN List
Service n°47: Mailbox Dialling Numbers
Service n°48: Message Waiting Indication Status
Service n°49: Call Forwarding Indication Status
Service n°50: Reserved and shall be ignored
Service n°51: Service Provider Display Information
Service n°52 Multimedia Messaging Service (MMS)
Service n°53 Extension 8
Service n°54 Call control on GPRS by USIM
Service n°55 MMS User Connectivity Parameters
Service n°56 Network's indication of alerting in the MS (NIA)
Service n°57 VGCS Group Identifier List (EFVGCS and EFVGCSS)
Service n°58 VBS Group Identifier List (EFVBS and EFVBSS)
Service n°59 Pseudonym
Service n°60 User Controlled PLMN selector for I-WLAN access
Service n°61 Operator Controlled PLMN selector for I-WLAN access
Service n°62 User controlled WSID list
Service n°63 Operator controlled WSID list
Service n°64 VGCS security
Service n°65 VBS security
Service n°66 WLAN Reauthentication Identity
Service n°67 Multimedia Messages Storage
Service n°68 Generic Bootstrapping Architecture (GBA)
Service n°69 MBMS security
Service n°70 Data download via USSD and USSD application mode
Service n°71 Equivalent HPLMN
Service n°72 Additional TERMINAL PROFILE after UICC activation
Service n°73 Equivalent HPLMN Presentation Indication
Service n°74 Last RPLMN Selection Indication
Service n°75 OMA BCAST Smart Card Profile
Service n°76 GBA-based Local Key Establishment Mechanism
Service n°77 Terminal Applications
Service n°78 Service Provider Name Icon
Service n°79 PLMN Network Name Icon
Service n°80 Connectivity Parameters for USIM IP connections
Service n°81 Home I-WLAN Specific Identifier List
Service n°82 I-WLAN Equivalent HPLMN Presentation Indication
Service n°83 I-WLAN HPLMN Priority Indication
Service n°84 I-WLAN Last Registered PLMN
Service n°85 EPS Mobility Management Information
Service n°86 Allowed CSG Lists and corresponding indications
Service n°87 Call control on EPS PDN connection by USIM
Service n°88 HPLMN Direct Access
Service n°89 eCall Data
Service n°90 Operator CSG Lists and corresponding indications
Service n°91 Support for SM-over-IP
Service n°92 Support of CSG Display Control
Service n°93 Communication Control for IMS by USIM
Service n°94 Extended Terminal Applications
Service n°95 Support of UICC access to IMS
Service n°96 Non-Access Stratum configuration by USIM
Service n°97 PWS configuration by USIM
QUESTION 2
An officer approaches you as the expert to investigate comminucations on an iPhone. There is known comms that have taken place but the twist is the comms at the distance end are being received by a Satellite phone. The user of the SatPhone is known to be trafficking in young children snatched from parents whilst on holiday. Your job is to provide evidence to help the police officer regarding which elementary files in the USIM would be used to permit mobile network usage (home and roaming) and any network artefacts that maybe connected to Satellite comms? To help you, a link below leads you to a piece of equipment that links iPhone to satellite:
www.thuraya.com/
QUESTION 1
There are at minimum 1,900 items for examination discovery, investigatory leads and evidence that can be obtained from these UST entries. Can you identify just 50 items for examination discovery, investigatory leads and evidence? If so, what are they?
Service n°1: Local Phone Book
Service n°2: Fixed Dialling Numbers (FDN)
Service n°3: Extension 2
Service n°4: Service Dialling Numbers (SDN)
Service n°5: Extension3
Service n°6: Barred Dialling Numbers (BDN)
Service n°7: Extension4
Service n°8: Outgoing Call Information (OCI and OCT)
Service n°9: Incoming Call Information (ICI and ICT)
Service n°10: Short Message Storage (SMS)
Service n°11: Short Message Status Reports (SMSR)
Service n°12: Short Message Service Parameters (SMSP)
Service n°13: Advice of Charge (AoC)
Service n°14: Capability Configuration Parameters 2 (CCP2)
Service n°15: Cell Broadcast Message Identifier
Service n°16: Cell Broadcast Message Identifier Ranges
Service n°17: Group Identifier Level 1
Service n°18: Group Identifier Level 2
Service n°19: Service Provider Name
Service n°20: User controlled PLMN selector with Access Technology
Service n°21: MSISDN
Service n°22: Image (IMG)
Service n°23: Support of Localised Service Areas (SoLSA)
Service n°24: Enhanced Multi Level Precedence and Pre emption Service
Service n°25: Automatic Answer for eMLPP
Service n°26: RFU
Service n°27: GSM Access
Service n°28: Data download via SMS-PP
Service n°29: Data download via SMS CB
Service n°30: Call Control by USIM
Service n°31: MO-SMS Control by USIM
Service n°32: RUN AT COMMAND command
Service n°33: shall be set to '1'
Service n°34: Enabled Services Table
Service n°35: APN Control List (ACL)
Service n°36: Depersonalisation Control Keys
Service n°37: Co-operative Network List
Service n°38: GSM security context
Service n°39: CPBCCH Information
Service n°40: Investigation Scan
Service n°41: MexE
Service n°42: Operator controlled PLMN selector with Access Technology
Service n°43: HPLMN selector with Access Technology
Service n°44: Extension 5
Service n°45: PLMN Network Name
Service n°46: Operator PLMN List
Service n°47: Mailbox Dialling Numbers
Service n°48: Message Waiting Indication Status
Service n°49: Call Forwarding Indication Status
Service n°50: Reserved and shall be ignored
Service n°51: Service Provider Display Information
Service n°52 Multimedia Messaging Service (MMS)
Service n°53 Extension 8
Service n°54 Call control on GPRS by USIM
Service n°55 MMS User Connectivity Parameters
Service n°56 Network's indication of alerting in the MS (NIA)
Service n°57 VGCS Group Identifier List (EFVGCS and EFVGCSS)
Service n°58 VBS Group Identifier List (EFVBS and EFVBSS)
Service n°59 Pseudonym
Service n°60 User Controlled PLMN selector for I-WLAN access
Service n°61 Operator Controlled PLMN selector for I-WLAN access
Service n°62 User controlled WSID list
Service n°63 Operator controlled WSID list
Service n°64 VGCS security
Service n°65 VBS security
Service n°66 WLAN Reauthentication Identity
Service n°67 Multimedia Messages Storage
Service n°68 Generic Bootstrapping Architecture (GBA)
Service n°69 MBMS security
Service n°70 Data download via USSD and USSD application mode
Service n°71 Equivalent HPLMN
Service n°72 Additional TERMINAL PROFILE after UICC activation
Service n°73 Equivalent HPLMN Presentation Indication
Service n°74 Last RPLMN Selection Indication
Service n°75 OMA BCAST Smart Card Profile
Service n°76 GBA-based Local Key Establishment Mechanism
Service n°77 Terminal Applications
Service n°78 Service Provider Name Icon
Service n°79 PLMN Network Name Icon
Service n°80 Connectivity Parameters for USIM IP connections
Service n°81 Home I-WLAN Specific Identifier List
Service n°82 I-WLAN Equivalent HPLMN Presentation Indication
Service n°83 I-WLAN HPLMN Priority Indication
Service n°84 I-WLAN Last Registered PLMN
Service n°85 EPS Mobility Management Information
Service n°86 Allowed CSG Lists and corresponding indications
Service n°87 Call control on EPS PDN connection by USIM
Service n°88 HPLMN Direct Access
Service n°89 eCall Data
Service n°90 Operator CSG Lists and corresponding indications
Service n°91 Support for SM-over-IP
Service n°92 Support of CSG Display Control
Service n°93 Communication Control for IMS by USIM
Service n°94 Extended Terminal Applications
Service n°95 Support of UICC access to IMS
Service n°96 Non-Access Stratum configuration by USIM
Service n°97 PWS configuration by USIM
QUESTION 2
An officer approaches you as the expert to investigate comminucations on an iPhone. There is known comms that have taken place but the twist is the comms at the distance end are being received by a Satellite phone. The user of the SatPhone is known to be trafficking in young children snatched from parents whilst on holiday. Your job is to provide evidence to help the police officer regarding which elementary files in the USIM would be used to permit mobile network usage (home and roaming) and any network artefacts that maybe connected to Satellite comms? To help you, a link below leads you to a piece of equipment that links iPhone to satellite:
www.thuraya.com/
Saturday, March 15, 2014
SIM Test Card Hardware Layouts
15/11/97
Interface for ASIM
README This file.
EMUSIM.BMP Artwork of Smart Card sized PCB
MAX232.BMP Artwork of Smart Card sized PCB whith MAX232
MAX232LY.GIF Parts placement guide of max232 pcb.
CIRCLAY.GIF Parts placement guide.
The bitmap file can be loaded into Windows Paintbrush then printed. They
are drawn 1:1 at 300 dpi so make sure you click "Use printer resolution" and
the Laser printer is set to 300 dpi before you print. The artwork is drawn as
seen from the copper side. It can be printed on a transparency as is and used
directly in a positive photo etch. The copper side of PCB not touches the
toner side of transparency.
Bye
by Giulio Cesare
SIM/USIM Research Materials
Research Materials
I shall be posting material (example below) I have gathered from my research over the last 20 years that students, examiners and experts may find of use. Some of the materials to be posted I couldn't find when I searched the Internet recently. Whether that is down to me not searching enough or information held in web-based wall-gardens or the information is no longer available, it would be a pity to let that research fade into obscurity. Where I can identify authors of materials posted I shall do so. But if I cannot do that then by posting I am not declaring someone elses work or their material are my creation. I am just sharing what is and in some case what was freely distributed over the years.
Trial and Error
When considering historical material it can provide a useful background insight, whilst at the same time nuture the interest to experiment and offers a knowledge base that may be needed or useful to know when approaching trial and error tests/experimentation.
Past Solutions Future Answers
One last point. A re-occuring theme, when considering digital evidence or forensic methodology or, even, how to apply examination techniques, is that solutions to problems, conundrums or perceived diametrically opposing facts can often be found by studying early developments in particular technologies. The approach that the manufacturer applied to the technology or how research and application found another way through may provide the solution for students, examiners and experts.
TEST SIM Script
(NOTE: The only details I have for the Author "brka". The email and website are no longer active. It is possible that the test materials are compiled from different sources and brought together in one source file. Some of the materials seemed to be have recognisable or at least similar designs to that created by the known programmer/developer "Dejan").
Once when you make TEST SIM using test_sim.hex you can:
Entering into TEST mode
***********************
Insert TEST SIM in your phone.
Power ON phone.
When phone ask for PIN, type 5555
Then, the phone displays "CHECK CARD",
and then Power-Off the phone and Power-Up
The phone will enter into the TEST mode ....
(it can Register on ANY network ... but no Phone calls
can be done)
Entering into CLONE mode (SP Unlocking)
***************************************
Insert TEST SIM in your phone.
Power ON phone.
When phone ask for PIN, type 1111
Phone will display "CHECK CARD"
Wait for few seconds and turn OFF phone!!!
Now turn phone ON and phone will be in CLONE Mode!
Clone Mode works on all Motorola phones!
SP Unlocking
************
Once you are in Clone Mode, type 03# and phone will be unlocked.
NOTE! SP unlocking work on all Motorola phones made before Sep.98!!!
It even works on some of CD920 and CD930 ....
Try it and please write me the results ....
(I found that the phones that IMEI ends with 0 can be unlocked !)
TEST SIM can be made with PIC 16F84 (16C84) wafer card.
***************************************
test_sim.hex
***************************************
This test file is still available on the internet
Tools
PICkit - http://www.microchip.com/Developmenttools/ProductDetails.aspx?PartNO=PG164130
Propic2 Clone - http://cuteminds.com/index.php/en/propic2
I shall be posting material (example below) I have gathered from my research over the last 20 years that students, examiners and experts may find of use. Some of the materials to be posted I couldn't find when I searched the Internet recently. Whether that is down to me not searching enough or information held in web-based wall-gardens or the information is no longer available, it would be a pity to let that research fade into obscurity. Where I can identify authors of materials posted I shall do so. But if I cannot do that then by posting I am not declaring someone elses work or their material are my creation. I am just sharing what is and in some case what was freely distributed over the years.
Trial and Error
When considering historical material it can provide a useful background insight, whilst at the same time nuture the interest to experiment and offers a knowledge base that may be needed or useful to know when approaching trial and error tests/experimentation.
Past Solutions Future Answers
One last point. A re-occuring theme, when considering digital evidence or forensic methodology or, even, how to apply examination techniques, is that solutions to problems, conundrums or perceived diametrically opposing facts can often be found by studying early developments in particular technologies. The approach that the manufacturer applied to the technology or how research and application found another way through may provide the solution for students, examiners and experts.
TEST SIM Script
(NOTE: The only details I have for the Author "brka". The email and website are no longer active. It is possible that the test materials are compiled from different sources and brought together in one source file. Some of the materials seemed to be have recognisable or at least similar designs to that created by the known programmer/developer "Dejan").
Once when you make TEST SIM using test_sim.hex you can:
Entering into TEST mode
***********************
Insert TEST SIM in your phone.
Power ON phone.
When phone ask for PIN, type 5555
Then, the phone displays "CHECK CARD",
and then Power-Off the phone and Power-Up
The phone will enter into the TEST mode ....
(it can Register on ANY network ... but no Phone calls
can be done)
Entering into CLONE mode (SP Unlocking)
***************************************
Insert TEST SIM in your phone.
Power ON phone.
When phone ask for PIN, type 1111
Phone will display "CHECK CARD"
Wait for few seconds and turn OFF phone!!!
Now turn phone ON and phone will be in CLONE Mode!
Clone Mode works on all Motorola phones!
SP Unlocking
************
Once you are in Clone Mode, type 03# and phone will be unlocked.
NOTE! SP unlocking work on all Motorola phones made before Sep.98!!!
It even works on some of CD920 and CD930 ....
Try it and please write me the results ....
(I found that the phones that IMEI ends with 0 can be unlocked !)
TEST SIM can be made with PIC 16F84 (16C84) wafer card.
***************************************
test_sim.hex
***************************************
This test file is still available on the internet
Tools
PICkit - http://www.microchip.com/Developmenttools/ProductDetails.aspx?PartNO=PG164130
Propic2 Clone - http://cuteminds.com/index.php/en/propic2
Labels:
experimentation,
PIC 16C84,
PIC 16F84,
research,
SIM/USIM,
trial and error
Sunday, October 06, 2013
(U)ICC/(U)SIM Script Commands and Responses
(U)ICC/(U)SIM 3F00 7F10 6F4A
3GPP UICC/USIM script selecting Master File, Dedicated File and Elementary File
GSM ICC/SIM script selecting Master File, Dedicated File and Elementary File
Reason for script test : defining an examination procedure to isolate and test a single elementary file; determine the EF's status, file structure, coding etc; conrroborate the ability of the (U)ICC/(U)SIM to action responses from commands sent to card; provide corroborating evidence of commands sent to the card to demonstrate evidential integrity (transparency of practices and procedures); testing the examination card reader is functioning correctly; QA procedures.
Script examination tool used : USIM Commander - http://www.quantaq.com/usimcommander.htm
Relevant Core Diplomas:-
Aims : MTEB Diploma for Mobile Evidence QA and Evidence Handling - Mobile Telephone Diploma Core CQAE1
Objectives : Device Maintenance and Calibration; Examination Procedure
Aims : MTEB Diploma for SIM and USIM Technology Examination - Mobile Telephone
Diploma Core CSUT2
Objectives : Your understanding of roles and responsibilities and the importance of
appropriate practices and procedures for SIM and USIM Technology
Examination for acquiring evidence.
Reference Standards :
GSM11.11/3GPP TS51.011/3GPP TS31.102,
GSM11.12,
GSM11.17/3GPP TS51.017/3GPP TS31.120/3GPP TS31.121/3GPP TS31.122,
GSM11.18/3GPP31.101,
EU MTEB Diploma Student Note : Remember to check with ETSI Standards e.g. TS102.221 etc
US MTEB Diploma Student Note : Diploma Students remember to check e.g. C.S0065-0 v1.0, C.S0074-0 v1.0, C.S0074-A v1.0, N.S0009-0 v1.0, S.R0095-0 v1.0 etc
Generically speaking, apart from GSMA and 3GPP, there is also 3GPP2 which also includes ARIB, CCSA, TIA TTA, TTC that all have conditions that can impact/influence results on (U)ICC/(U)SIM.
The discussion under (U)ICC/(U)SIM Script Commands and Responses is one of a number that will appear here to assist Diploma students with their course work.
The latest MTEB Diploma Modules Guide MTEdipl 2.2 can be downloaded here:
https://dl.dropboxusercontent.com/u/84491783/MTEdipl%202.2.pdf
Labels:
3GPP/3GPP2,
ARIB,
CCSA,
Dedicated File,
Diploma,
Elementary Files,
EU,
evidence,
examination procedure,
GSMA,
ICC,
Master File,
SIM,
TIA TTA,
TTC,
UICC,
US,
USIM
Saturday, September 28, 2013
MTEB Diploma CSUT2 Partner

Diploma for SIM and USIM Technology Examination
Mobile Telephone Diploma Core
Diploma:CSUT2
Partner Support
The Mobile Telephone Examination Board (MTEB) are pleased announce that Quantaq Solutions (http://www.quantaq.com/about.htm) have agreed to be the MTEB Diploma CSUT2 Partner. Quantaq Solutions role is as a "Partner Support". This role entails
- providing trial copies of software
- respond to technical enquiries that a student may require to make
to assist with the student's Diploma.
Moreover, Quantaq Solutions will host an MTEB webpage solely for use by MTEB Diploma Students so that students can have acess to the software and post questions to seek technical assistance.
SIM, smartcards, NFC, RFID, M2M, location, DRM, security, cryptography, Mobile Wallet, technology, innovation, patents, technical design authority, standardisation, proof-of-concepts and software development
Gary Waite
Leading the "Partner Support" on behalf of Quantaq Solutions is Gary Waite. Gary is very well known in the mobile forensics arena for his work on the tools the (U)SIM forensic tools USIM Detective (USIM-D) and USIM Detective Professional (USIM-DP).
His experience and technical background further underpin his credentials of his expertise:
- Founder of Quantaq Solutions
- Past Vice Chair of the Smart Card Group GSM Association
- Test software supplier to Global Certification Forum (GCF) Field Trial Guidelines
- Authored the original ETSI GSM 11.17 standard. This standard formalised the core test processes and procedures for SIM Cards and remains at the heart of (U)SIM testing, programming and examination today.
- First to introduce recording in CUST File (EF) a particular handset's IMEI on SIM Card, which is important, evidentially
- Employed as Technology Manager for the last 11 years with a well know international Mobile Network Operator
- Skilled in C/C++/Java
- Holds a Degree from the University of Abertay Dundee - Electrical & Electronic Engineering, Electronic Engineering
Diploma:CSUT2
Free trial access to the following tools will be made available to Diploma Students.
USIMdetective - http://www.quantaq.com/usimdetective.htm
USIMexplorer - http://www.quantaq.com/usimexplorer.htm
USIMexplorer - http://www.quantaq.com/usimcommander.htm
USIMprofiler - http://www.quantaq.com/usimprofiler.htm
Diploma for SIM and USIM Technology Examination
Mobile Telephone Diploma Core
Diploma:CSUT2
The latest MTEB Diploma Modules Guide is MTEdipl 2.2 can be downloaded here:
https://dl.dropboxusercontent.com/u/84491783/MTEdipl%202.2.pdf
Saturday, September 14, 2013
Blocked SIM
A regular question that arises, "is it possible to bypass a PIN blocked SIM card?"
For a quick solution it is best to go to the operator to obtain a PUK code where there has been 3 CHV1 attempts and access is now blocked.
If it is 10 CHV1 attempts and blocked ([unless you know and have the test tools to e.g. slow the card]) then the operator may request that you send it to them and they in turn (depending upon their security level) may need to send it to the (U)ICC producer / manufacturer.
Today's UICC (using improved silicon and security techniques) have significant security improvements within each operator's card where there are various levels of electronic counter-measures (traps doors/dead-man's trap etc). Many of us (including me) simply cannot access certain areas of the UICC unless a flaw in the security is discovered. Unless you are confident of what you know and what you are doing, my observation is take the safest route.
None of the opinions I express originate based upon my gut feeling about a particular matter. I research, like others, to establish the industry security protocols, practices and procedures and then consider the position from there. It is important to bare in mind that forensics and evidence is not about hacking everything in sight or writing a program to extract data but to be aware and comprehend how industry standard bodies intended security should be implement, which norms the manufacturer and operator follow and whether following implementation security flaws occur.
For a quick solution it is best to go to the operator to obtain a PUK code where there has been 3 CHV1 attempts and access is now blocked.
If it is 10 CHV1 attempts and blocked ([unless you know and have the test tools to e.g. slow the card]) then the operator may request that you send it to them and they in turn (depending upon their security level) may need to send it to the (U)ICC producer / manufacturer.
Today's UICC (using improved silicon and security techniques) have significant security improvements within each operator's card where there are various levels of electronic counter-measures (traps doors/dead-man's trap etc). Many of us (including me) simply cannot access certain areas of the UICC unless a flaw in the security is discovered. Unless you are confident of what you know and what you are doing, my observation is take the safest route.
None of the opinions I express originate based upon my gut feeling about a particular matter. I research, like others, to establish the industry security protocols, practices and procedures and then consider the position from there. It is important to bare in mind that forensics and evidence is not about hacking everything in sight or writing a program to extract data but to be aware and comprehend how industry standard bodies intended security should be implement, which norms the manufacturer and operator follow and whether following implementation security flaws occur.
Subscribe to:
Comments (Atom)