





As the device has been programmed, and looking at the on-board chip, there should be a reader for it or one could be constructed. This throws me back to the old days of ponyprog and PIC basics. Of course, of equal importance is how does this device impact when examining the handset and SIM card? Will manual examination be the only course for examination or do the current handset and SIM readers detect changes this device makes to them? What evidence is there for call history or data usage? These are just a few of the questions to get examiners started.


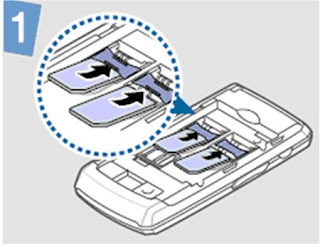
This mobile phone is capable of having two SIM cards inserted, at the same time, in order to allow for two different subscriber accounts to be used separately by a user. To understand the difference compare the position when dealing with the traditional way of having to manually swop a SIM card with another in a device that is a single-inserted SIM card operating mobile phone.
.
Once the user has selected to use one of the two SIM Cards inserted, the option to switch to a particular SIM in normal user mode is via the 'SIM selection key' with visual Icons displayed on the device's screen confirming which SIM and subscription account is in use.

1) Take out one of the user SIM cards and produce a cloned test SIM card, whilst leaving the other user SIM card in place? Then insert the new clone test SIM card and then examine the phone? It is unlikely this could work well because an original user SIM card is still in place, thus the mobile phone could still register to the network etc. That is so, because the examiner doesn't know which SIM and subscription account was last used by the mobile phone. The notion of switching the mobile phone 'ON' prior to using a cloned Test SIM card to find out begs the question why is the examiner using cloned test SIM cards in the first place?
2) Take out both user SIM cards and produce two cloned test SIM cards, but insert only one test card and examine on that basis? This might work, provided of course the examiner has selected for access the right SIM slot and subscription account, which is a bit 'trial and error', 'hit and miss'? Moreover, assuming the above method had worked and the examiner safely selected the correct SIM slot/account - for example by taking the pragmatic step of recording which user SIM came out of which slot and replacing the correct cloned test SIM card into the slot - what happens when the second cloned test SIM card needs to be inserted? Using the SIM selection key to switch to another SIM card may not assist because there isn't a cloned test SIM card in the second slot for the device to read any details. Moreover, bearing in mind the device memory has noted only one SIM inserted the first time around what impact might now happen if a second cloned test SIM card is inserted? Will it allow access to the subscriber account user data on the device? Furthermore, what happens when switching over to the other cloned test SIM card?
.
If you work in forensics and/or examination devices, investigations or deal with evidence then the MTEB forum puts you in contact with other professionals when you need help with technical issues, technical discussions or generally want to stay up to date. Due to the make up of the forum members: experts, high level security, law enforcement and senior investigators requests to join are vetted.
.
.
Invitation to Join Mobile Telephone Examination Board
--------------------------------------------------------
The MTEB forum is dedicated to evidential standards, forensic examination and lawful interception dealing with mobile telephones/SIM/USIM/MMC, bluetooth, IrDA, USB, cell site analysis and mobile networks GSM, CDMA, 3G, 4G.
.
Link if you are NOT a LinkedIn member:
http://www.linkedin.com/groupInvitation?groupID=141739&sharedKey=35E59F107179
Link if you are a LinkedIn member:
http://www.linkedin.com/groupsDirectory?results=&sik=1216135556335
